Sustainable water management
According to the United Nations, despite increases in water use efficiency, water scarcity remains a concern, and billions of people lack access to safe water, sanitation and hygiene.
To combat this crisis, sustainable consumption is promoted, the promotion of clean energy, the optimization of production processes and the use of recycled water.
Sustainable water management is crucial to ensure equitable, affordable and safe access to this vital resource, as well as to preserve aquatic ecosystems and address the challenges of sustainable development.
Challenges in water management
The challenges in water management are diverse and require comprehensive solutions that address both technical and environmental and sustainability aspects. We face the overexploitation of aquifers, pollution, lack of access to drinking water and climate change.
Several of the challenges in water management include:
These challenges are fundamental to guarantee the availability and sustainable use of water in the future, addressing aspects of access, sustainability, efficiency and adaptation to climate change.
How does climate change affect water management?
Climate change alters precipitation patterns, resulting in increased soil moisture and, in turn, impacting water runoff.
Climate change is expected to cause greater variability in water resources, which could lead to more frequent and longer droughts in already arid regions, as well as intensified floods and storms.
Melting glaciers and rising sea levels are direct effects of climate change that affect water availability and quality. Climate change poses additional challenges for water management, especially in water-stressed regions, requiring effective and sustainable adaptation in water resource management.
Promote sustainable water consumption
Sustainable water management involves recovering the balance between freshwater consumption and its natural renewal, as well as promoting responsible and efficient use of the resource.
To encourage sustainable water consumption, several measures must be taken. These involve the reuse of water, the collection and storage of rainwater, the optimization of production processes, the use of recycled water and raising awareness about the importance of responsible use of water.
In addition, it is essential to promote efficient agriculture, repair leaks and leaks, and use technologies that allow more efficient use of water in all sectors.
These actions are essential to guarantee the future availability of water and preserve this vital resource for life on our planet.

SEWDEF and sustainable water management
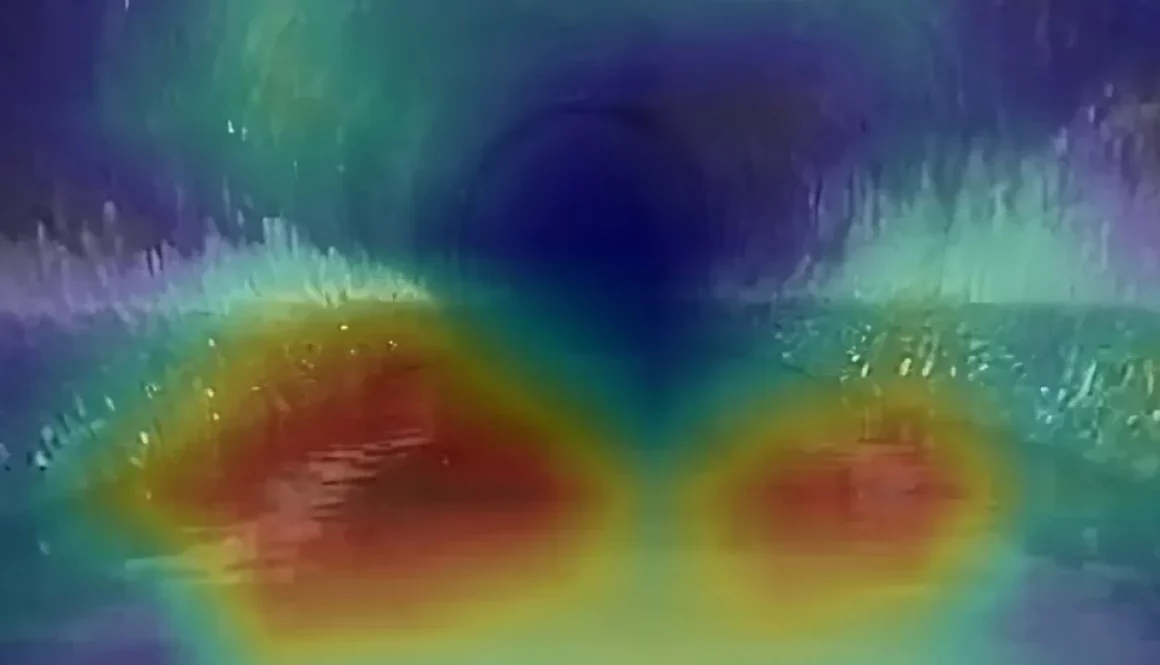
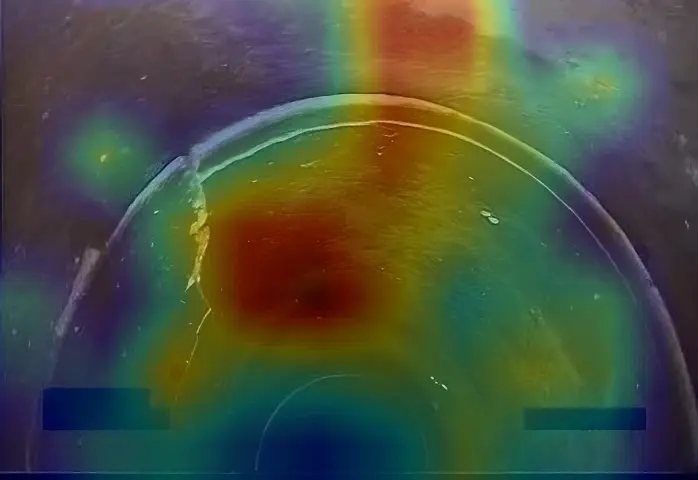
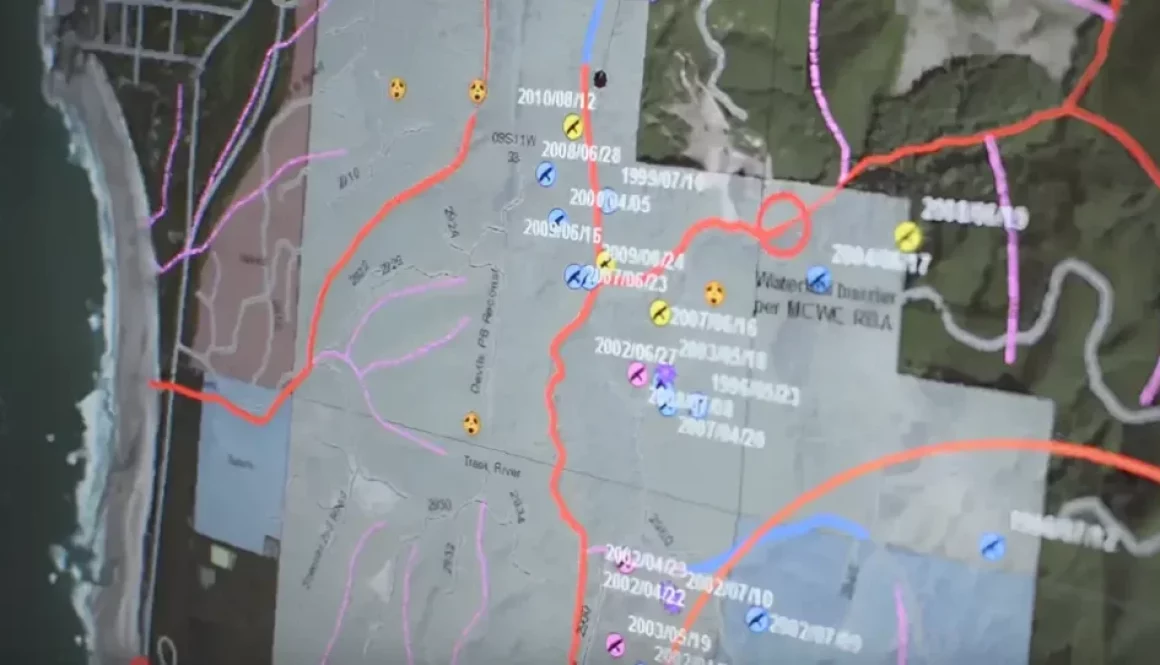
When it comes to improving and generating impact, we rely on the use of technology and digitalization. And this is where our SEWDEF service, an artificial intelligence-based automatic sewer network defect detection system, analyzes sewer network videos for defects and displays information on the condition and performance of the sewer system.
To learn more about the SEWDEF system:
How is more sustainable water management achieved?
To achieve more sustainable water management, various actions can be implemented at the individual, community and government levels. Some of these actions include:
It is essential to raise awareness among the population about the responsible use of water and promote saving practices in the home, agriculture and industry.
The implementation of efficient technologies, such as more precise irrigation systems and water-saving appliances, contributes to reducing consumption.
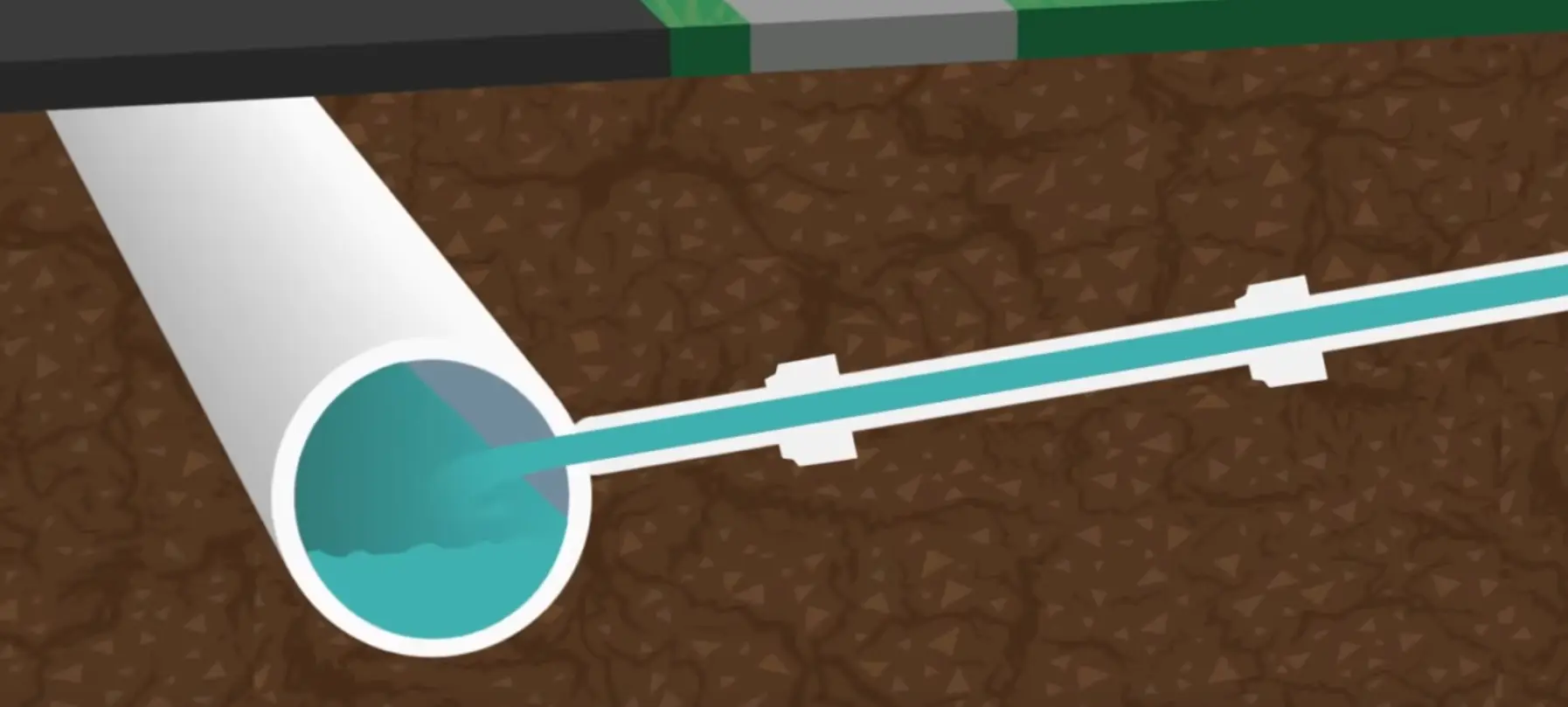
Develop and implement infrastructure that promotes sustainable water management, such as the capture and reuse of rainwater, and the detection and repair of leaks in distribution networks.
It is necessary to establish regulations and policies that promote the sustainable use of water, as well as incentives for the adoption of responsible practices.
In addition, at an individual level, there are several measures to take such as periodically checking the pipes and faucets at home to detect and repair leaks, using rainwater for non-potable uses, and limiting garden watering. These actions, combined with larger-scale efforts, contribute to more sustainable water management.
Benefits of good sustainable water management
Sustainable water management brings a series of economic, social and environmental benefits.
Economic benefits include job creation, fostering innovation and long-term cost reduction.
Socially, it guarantees equitable access to drinking water, improves health and promotes food security.
Environmentally, it contributes to the conservation of aquatic ecosystems, the protection of biodiversity and the mitigation of climate change. In addition, sustainable water management helps ensure a constant and reliable supply of crops, essential to meet food demand.
As we see, the benefits are multiple and in different areas.
Conclusion
Sustainable water management involves the responsible and efficient use and control of water to meet current needs without compromising its availability for future generations. It also involves planning and managing water demand, protecting its quality, managing water scarcity and adapting to climate change.
This approach is essential to ensure equitable, affordable and safe access to water, as well as to preserve aquatic ecosystems.
We hope this article has been useful to you. If you have an engineering project in hand and you think we can help you, here is the link where you can contact us and explain more about it.